BizMobile Go! Key Features
1. Advanced security
 Usage monitoring
Usage monitoring
Usage of devices is monitored 24/7. Devices with problems can be identified on the dashboard, and administrators without much specialized IT knowledge can quickly take measures to solve the problems.
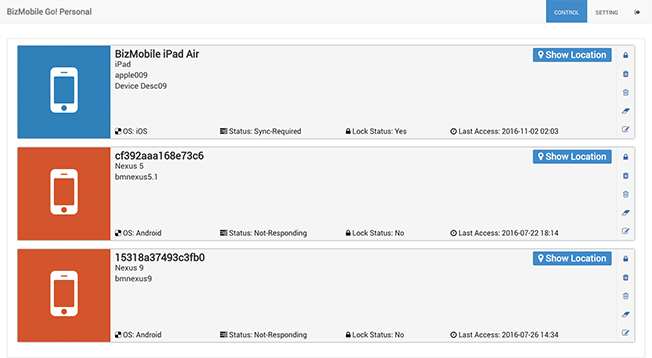
Dashboard
Risk of devices and their users can be managed using the dashboard. For example, an administrator can check devices that have not responded to the MDM system for longer than a specific period of time (unresponsive devices), installation of applications that pose problems to business operations (devices installed with prohibited applications), and usage of devices outside of job-related locations (location information).
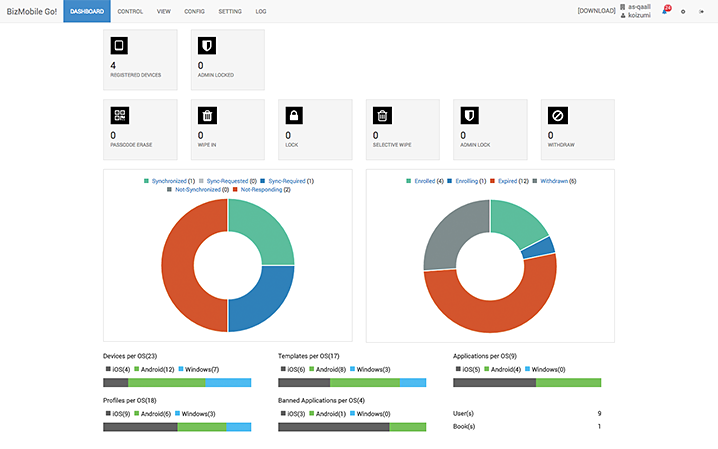
On the dashboard, an administrator can identify unresponsive devices and instantly move to an operation to take measures to solve the problem, such as locking, wiping, selective wiping, or administrator locking the device.
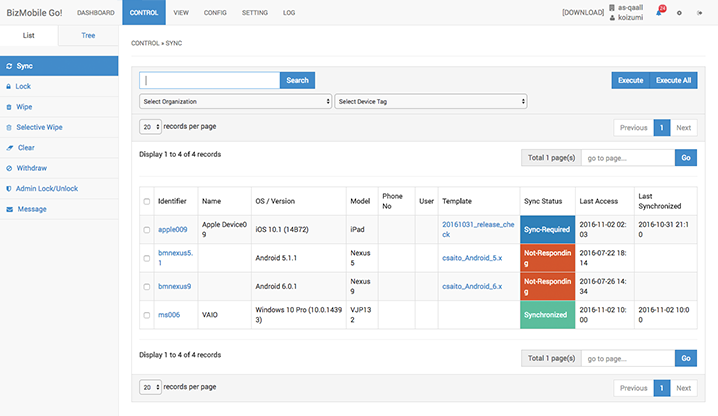
Alarm notifications
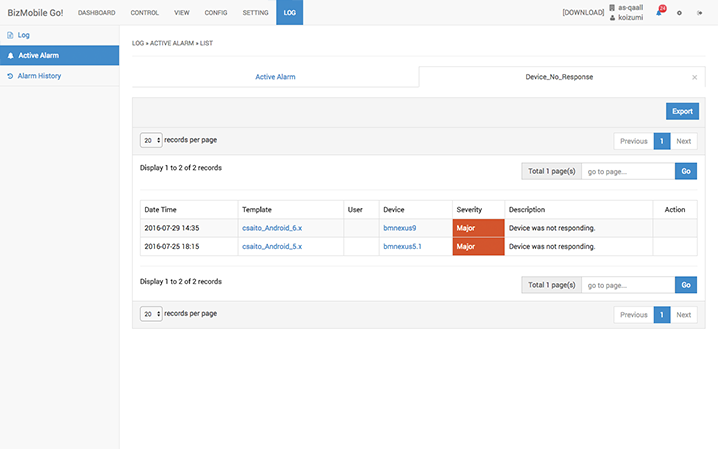
If an issue that requires review by an administrator occurs, an alarm notification will be sent out. A warning message will show up when a jailbreak or a root attempt is detected. When the problem is resolved, the alarm will be deactivated and the latest status will be shown. All alarms are saved for later review and information regarding problems that occurred are archived. It is possible to export all alarm records in a CSV file for analysis of alarm information.
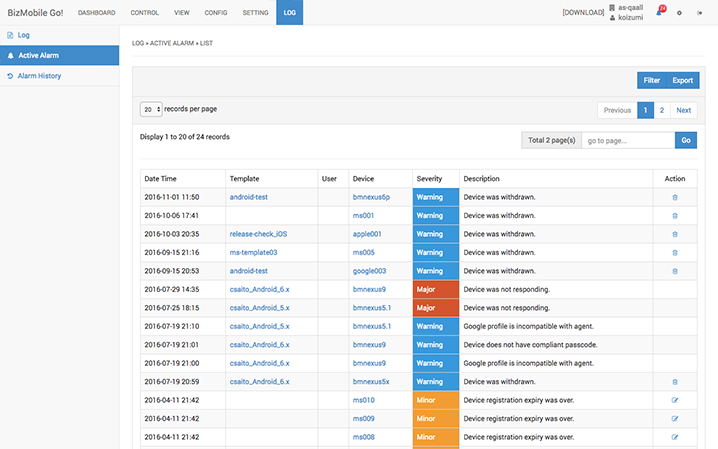
An administrator can filter the alarms and also use the tab function to monitor only problems of immediate concern. Creating tabs that are associated with alarm types will allow an administrator to manage multiple problems easily. Tabs can be deleted that are no longer necessary. Alarm information can be filtered and exported in a CSV file for analysis.
Detection of prohibited applications
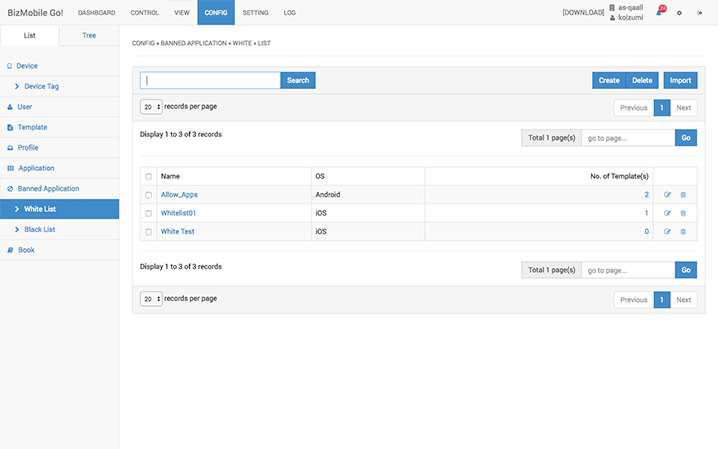
Applications that are prohibited by administrators can be specified using the whitelist/blacklist feature. Once a device with prohibited applications is detected, it will be shown up on the summary of devices with prohibited applications, so that an administrator can contact the owner of the device to delete the applications. Using the messaging function (optional service), users can be instructed directly by a short message.
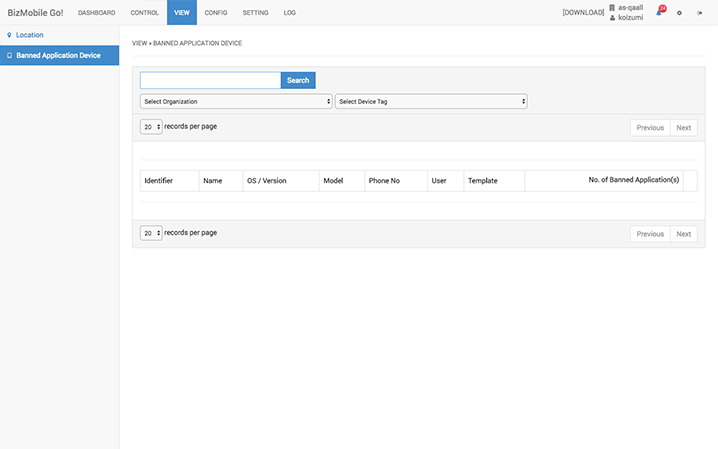
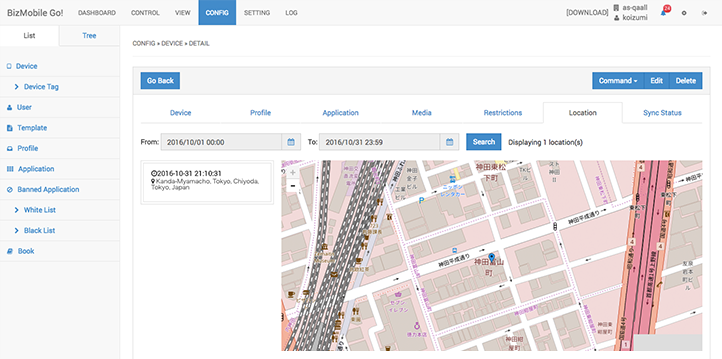
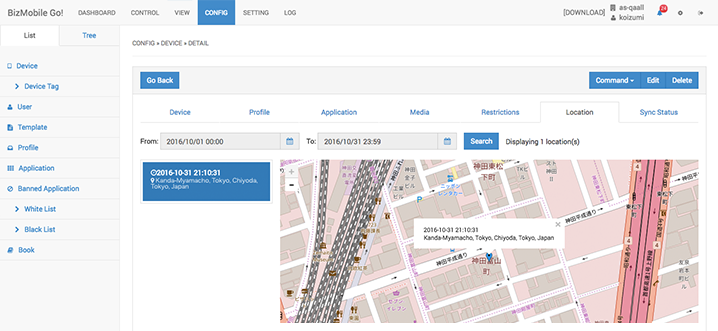
Display location information (optional)
After setting the number of times and the interval for which location information will be collected, all location information history will be shown for this period. For privacy protection, it is also possible to restrict review of device location information to the device user. (Works for BYOD as well)
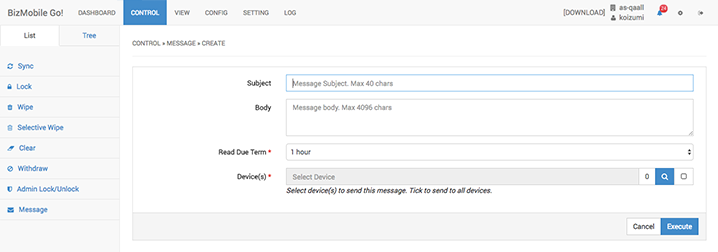
Messaging (optional)
Even when problems are identified remotely, it may not be always possible to take immediate actions to solve the problem remotely. There are also cases where confirmation with the user is desired, and where the administrator requires the user to perform some of the required tasks on the device. Typically, this would be done by sending an email. However, users often skip reading these emails or fail to do the required tasks after reading them. Hence, we have developed a function that allows messages to be sent to devices directly where the read/unread status of messages can be checked.
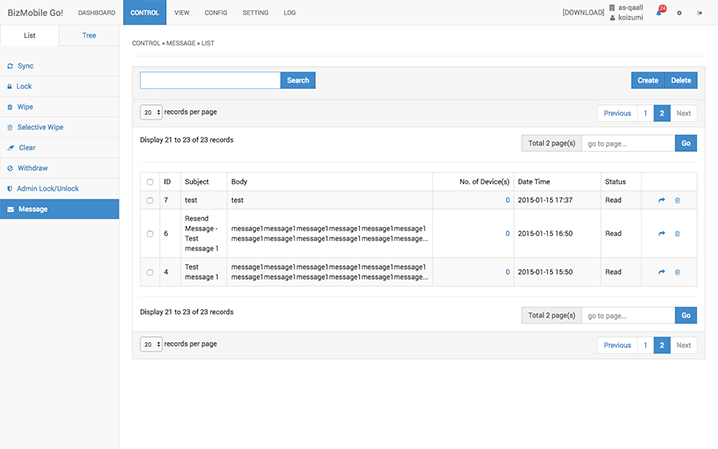
For messages that have been sent, it is possible to check whether users has received them, whether users have read them, whether users have yet to read them, how many users have read them, and who has yet to read them. It is also possible to resend messages.
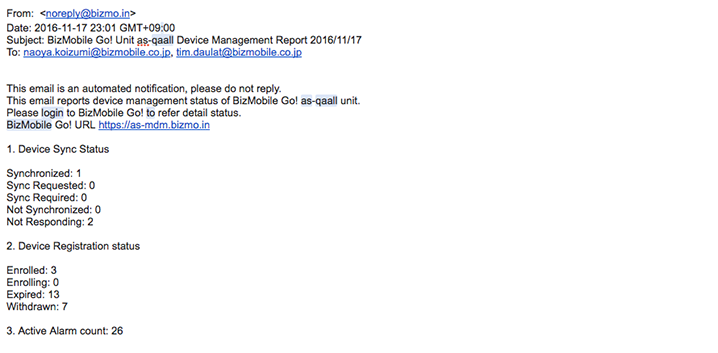
Device management status email
It is possible to send a daily email containing a summary of the device management status to multiple recipients at a specified time, under a fixed subject header. A link to the administrator user interface is provided in this email, so that if there are any problems reported, an administrator can immediately access the login page.
Summary of aspects monitored
| Aspects monitored | iOS 9 and above | Android 5.0 and above | Windows 8.1 and above |
| Total number of aspects monitored | 126 | 136 | 71 |
| Basic device information | 7 | 7 | 6 |
| Check-in restrictions | 8 | 7 | 4 |
| Device status | 8 | 8 | 7 |
| Settings/network status | 25 | 41 | 21 |
| Application list | 7 | 2 | |
| Status of functional restrictions | 69 | 69 | |
| Status of location information retrieval | 2 | 2 | |
| Disk drive | 7 | ||
| BIOS | 4 | ||
| Display | 2 | ||
| Network | 7 | ||
| Battery | 4 | ||
| Security | 3 | ||
| Shared drives | 3 | ||
| Service | 3 |
※All device monitoring data can be exported in a CSV file.
To find out more details about monitoring, please click here.
To find out more details about monitoring, please click here.
 Anti-loss/anti-theft measures
Anti-loss/anti-theft measures
BizMobile Go! has effective measures that can be taken in case of theft or loss, and when there is a risk of information leakage.
Lock & wipe
Once a lock or wipe command is issued to a specific device, the device will execute the lock or wipe immediately after connecting to the network, regardless of whether it is out of battery or in an area with no signal.
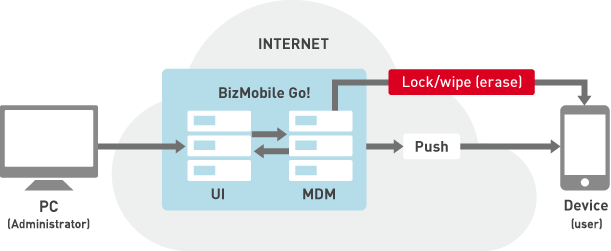
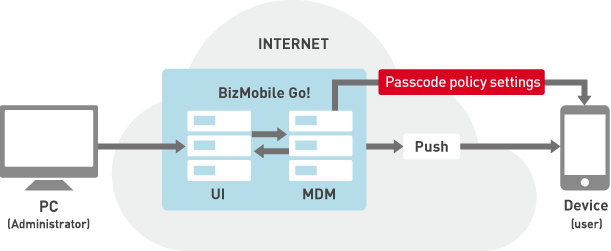
If a passcode policy is pre-configured on devices via the MDM service, a forced wipe and factory reset will be performed if the number of failed passcode attempts exceeds a specified amount, even if the device is not connected to the network.
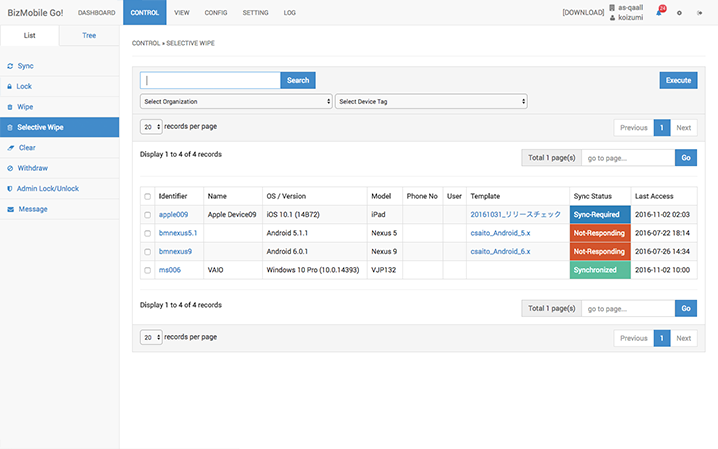
Selective wipe — Deletion of corporate data
The selective wipe function allows you to immediately delete only intellectual property belonging to your company, which offers a good balance between security and privacy. There is no risk in deleting personal information on BYOD(Bring Your Own Device) devices (personal devices used for business purposes). Once the device is recovered and is confirmed to be returned to the user, the deleted data can quickly be restored by reconfiguring enterprise information on the device, which does not sacrifice convenience.
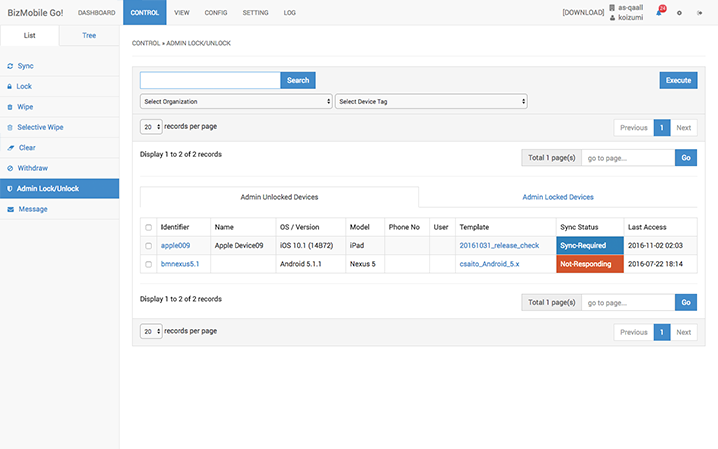
Immediate suspension of device usage (administrator lock: optional)
For devices offered by enterprises, preventing unauthorized usage by a malicious third party is not the only reason why they wish to immediately suspend operation of their devices. Resignations of employees and change of positions may also necessitate this function. The administrator lock function allows to immediately suspend device operation, that can only be lifted by the administrator.
Self-service user interface (personal UI: optional)
The self-service user interface is user-friendly and reduces workload of administrators, by allowing the user himself to take the necessary actions (lock, wipe) in case of theft or loss of a device. This service automatically invokes a notification to the administrator, so that there is no need for the user to contact the administrator.
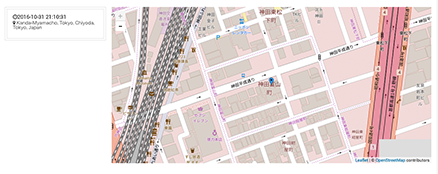
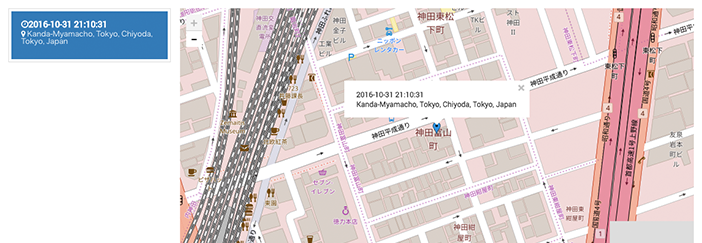
The self-service interface also allows users to trace where the device was lost or where the device has been moved, even if the device was lost in a taxi or a train. It safeguards privacy and allows the only the user himself to trace the location of the device. (Works for BYOD as well)
Lock and wipe by phone call (personal IVR: optional)
BizMobile Go! also comes with a service that allows you to lock and wipe a device via a phone call when a device is found to be missing, so that immediate action can be taken even without using a PC. When user discovers that his device is missing, he can immediately call the designated telephone number and follow the voice guidance given by the interactive voice response (IVR) system to lock or wipe the device.
Summary of anti-loss/anti-theft measures
| Anti-loss/anti-theft measures | iOS 8 | iOS 9 | Android 4.4 | Android 5.1 | Windows 8.1 | Windows 10 |
| Force passcode policy | ○ | ○ | ○ | ○ | ○ | ○ |
| Local lock | ○ | ○ | ○ | ○ | ○ | ○ |
| Local wipe | ○ | ○ | ○ | ○ | ○ | ○ |
| Remote lock | ○ | ○ | ○ | ○ | ○ | Mobile only |
| Remote wipe | ○ | ○ | ○ | ○ | ― | ○ |
| Selective wipe | ○ | ○ | × | ○ | ー | Planned in future release |
| Suspend device operation (administrator lock) | Planned in future release | Planned in future release | × | ○ | × | Planned in future release |
| Outsource interface (lock, wipe, etc.) | ○ | ○ | ○ | ○ | ○ | ○ |
| Self-service interface | ○ | ○ | ○ | ○ | ○ | ○ |
| Location information (separate agent app required) | ○ | ○ | ○ | ○ | Planned in future release | Planned in future release |
| Self-service (interactive voice response) | ○ | ○ | ○ | ○ | ○ | ○ |
 Prevention of unauthorized access
Prevention of unauthorized access
Jailbreak and root detection (optional)
While mobile devices can be made highly secure by restricting user access privileges, it is possible to make use of OS vulnerabilities to jailbreak or root a device to access areas that were previously inaccessible. Use of OS in a manner not intended by the developer will pose a big security risk, not to mention that it will void any support services for Apple devices. Hence, there is a need for an app that can detect when a device has been jailbroken or rooted, and immediately notify the administrator of it.
Restrictions for personal use
It is impossible to completely prevent consumer mobile devices from being used for personal purposes. However, it is possible for enterprises to offer devices to employees with security by segregating private and public information in the device, and implementing restrictions on personal usage. Devices offered by enterprises fall under 3 categories: 1) COPE (Corporate-Owned, Personal-Enabled) devices, where some personal usage is allowed, 2) COCM (Corporate-Owned, Corporate-Managed) devices, where personal usage is greatly restricted, and 3) COSU (Corporate-Owned, Single Use) devices, which are used only for specific tasks.
COCM and COSU devices must be placed in Supervised Mode for iOS, and Device Owner Mode for Android. This will cause a factory reset of the device, so devices should be placed in those modes when they are activated. It is not very advisable to change the mode of a device already in use to these modes, but they allow access to more restrictions, offer silent installation capability, and restrictions for communication channels. Hence, this is one thing that companies should definitely consider on top of the DEP (Device Enrollment Program: Apple’s mechanism to set MDM during activation of devices) when offering devices to be used for business purposes.
COCM and COSU devices must be placed in Supervised Mode for iOS, and Device Owner Mode for Android. This will cause a factory reset of the device, so devices should be placed in those modes when they are activated. It is not very advisable to change the mode of a device already in use to these modes, but they allow access to more restrictions, offer silent installation capability, and restrictions for communication channels. Hence, this is one thing that companies should definitely consider on top of the DEP (Device Enrollment Program: Apple’s mechanism to set MDM during activation of devices) when offering devices to be used for business purposes.
| OS type | COPE (Some personal usage allowed) | COCM (Personal usage greatly restricted) |
| iOS 9 | Functions that can be restricted: 47 | Functions that can be restricted: 30 (factory reset required) |
| Android 5.1 | Functions that can be restricted:32 | Functions that can be restricted:37 (factory reset required) |
| Windows 10 | Functions that can be restricted: 107 (partially supported and planned to be enhanced) | |
Communication channel restrictions
Communication channel restrictions include: 1) Global HTTP Proxy (Make all HTTP transmissions from the device pass through a designated proxy so that monitoring and access restrictions can be implemented), 2) Content filtering (Restrict access to certain URLs by the device), and 3) Always-on VPN connection.
If global HTTP Proxy is used, it is possible to implement usage restrictions on applications like LINE and Facebook during working hours, as well as restrictions on OS updates. If content filtering is used, URL access restrictions can be implemented and customized for each individual device using whitelists and blacklists. An always-on VPN connection allows all communication to pass through company network.
If global HTTP Proxy is used, it is possible to implement usage restrictions on applications like LINE and Facebook during working hours, as well as restrictions on OS updates. If content filtering is used, URL access restrictions can be implemented and customized for each individual device using whitelists and blacklists. An always-on VPN connection allows all communication to pass through company network.
Summary of features to prevent unauthorized access
| Function | Overview | iOS 9 | Android 4.4 | Android 5.1 | Windows 8.1 | Windows 10 |
| Functional restrictions | Allow some personal usage | ○ | × | ○ | × | ― |
| Functional restrictions | Greatly restrict personal usage | ○ | × | ○ | × | ○ |
| Per-App VPN | Force VPN connections to company network for business-related applications | ○ | × | ○ | × | ○ |
| Open In | Segregate public and private data, and prevent data transfer between the two domains | ○ | × | ○ | × | ○ |
| Global Proxy | Make all HTTP transmissions pass through a proxy | ○ | × | ○ | × | Mobile only |
| Content filter | Limit URLs that can be accessed by a device | ○ | × | ○ | × | ○ |
| Always-on VPN connection | Make all communication pass through company network. | ○ | × | ○ | × | ○ |